MS Information & Communication Technology / PhotoShop
Section
Welcome and Enjoy the Class!
Course Overview: Click on the topics below to see more!

Open allClose all
Instructions: Clicking on the section name will show / hide the section.
- 1
Augmented Reality
- ToggleWhat is Augmented Reality?
AR App Examples for Smartphone (2013)
Google Translate - Did you know:
Google Translate - Download this app!
Google purchased Word Lens and put those features in Google Glass and now in their app, Google Translate. The app has three main parts:
- translating text around you and in scanned photos,
- translating live conversations in two languages
- translating written text.
Using this app, all of your books can be read in any language!!!
Aurasma (2016)
Aurasma Studio - get started
- 2
PhotoShop
- ToggleCreate a New Species - Hybrid Tutorial handout (click on image below for video)
Cartoon Yourself (and make a funky Profile Pic)!
Addition: Masking Tutorial 2 (Pumpkin Boy) & Masking Tutorial 3
*
*
*
NOW IT IS YOUR TURN! - Project Work
The Surreal Wiki -- see examples
Surreal Art is getting so much attention because it lets an artist freely express his creativity, feelings and the way he thinks. It is the medium of art in which you can showcase your talent and creativity in the most meaningful and the most intangible way. This is the main reason why Surreal Art is getting so popular these days.
Jerry Uelsmann
Maggie Taylor Artist Video
------------------------------------------------------------------------
-----------------------------------------------

Learn & Teach




Do your best, be creative and provide your own branded solution for the AISZ 50th Anniversary logo this year!
Based on the handout you have received, make a Crocodile-Frog Hybrid and upload the .jpeg file here.
Based on the handout "I've Been Cartooned", upload the cartoon image here.
- 3
DIGITAL CITIZENSHIP IN A GLOBAL SOCIETY
- ToggleComputer Literacy / Computers Inside -- What is in There??
Information & Communication Literacy -- Keep up Your Proficiency and Professionalism / E-mail Compose & Inbox/Label Set-up
Evaluating Internet Sources / Reliable and Non-Reliable Websites
Cyber Safety / Security Online - browse the site for 5 mins
Computer Security -- Stay Alert - play games
- 4
INFORMATION PROCESSING: Office & Google Drive
- ToggleWord Processing / Template Creation / Google Docs -- Write and Cite Properly / Copyright / Zotero Citation Machine -- Bibliography
Word Counting Macro Program -- Frequency Dictionary
Excel / Spreadsheets -- Manage Your Data, use Formulae
Graphing -- Show your results in a graph
PowerPoint / Presentations -- Present Effectively
- 5
MULTIMEDIA & ANIMATION: Flash
- ToggleFlash & Actions Script -- Let's Make That Object Roll & Transform
- 6
COMPUTER PROGRAMMING - Html
- Toggle1. HTML -- Who cares about Flash Anymore?
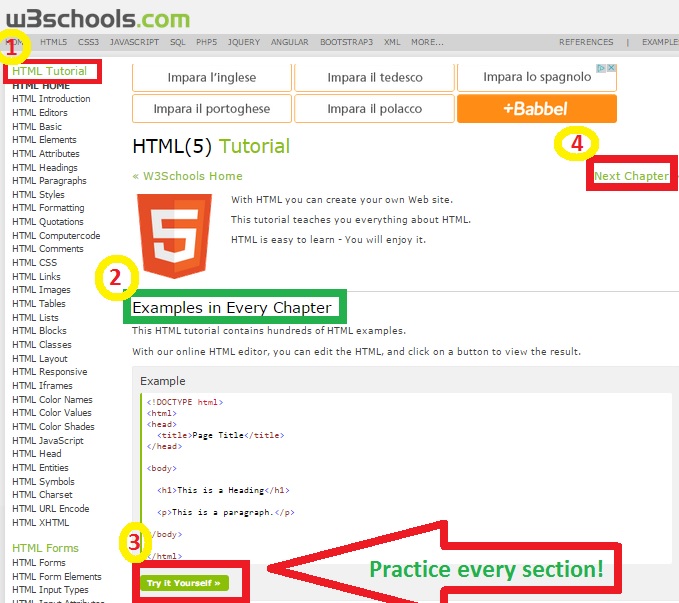
Navigate to W3 Schools and start learning HTML!
Go through every single section of HTML tutorials, study the given example, and by clicking the "Try it Yourself" button, practice what you have learned for every example.
2. BUILDING WEBSITES -- Blogs are Out! (this will follow after we learn HTML)
What is XHTML?
Current Assignment
- This section7
BUILDING MOBILE APPS - App Inventor
- ToggleApp Inventor -- Travelling home for Summer or Another Country? A Size or a Temperature Converter App on Your Phone Might Come in Handy Just in the Right Moment -- Let's Build It!!

Two assignments -- due Monday, May 18th!
BASIC LEVEL APPS
INTERMEDIATE LEVEL APPS
Blocks in App Inventor
ADVANCED LEVEL APPS
- 8
Programming in Scratch
- ToggleVisit this EdX course "Programming in Scratch", create and enroll (optional).

- 9
Introduction to Computer Science
- ToggleOn EdX, to look at Computer Science for Miidle Years course
THE COURSE STARTED!
- 10
Take a rest from class and play - BREAK TIME!!!
- Toggle - 11
Quiz
- Toggle










Social networks